
Breakdown of Microsoft’s Digital Defense Report 2024
Background
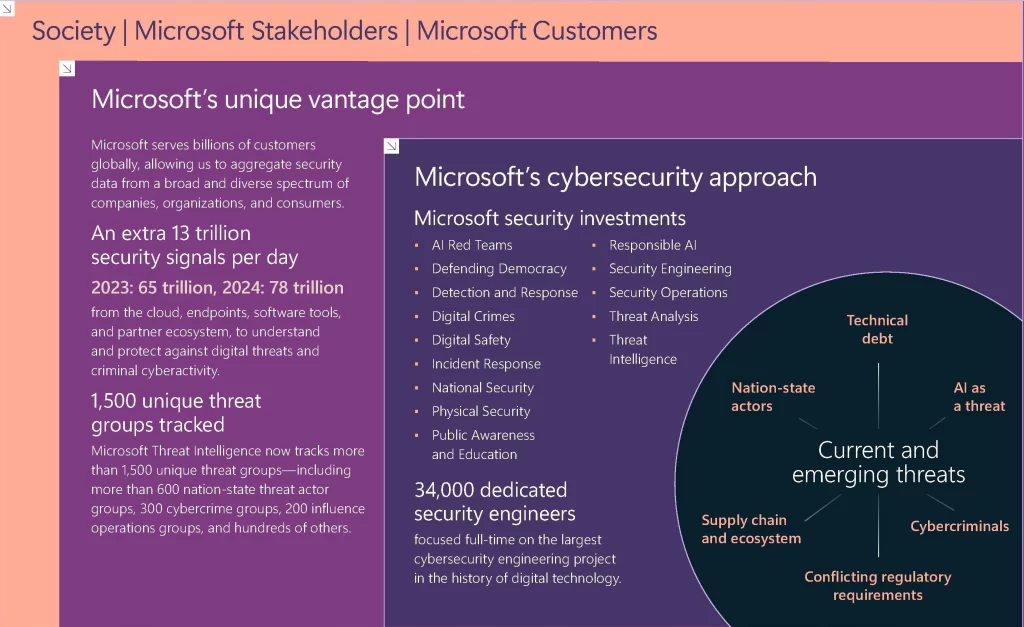
Microsoft’s latest Digital Defense Report 2024 provides insights into the evolving global cybersecurity landscape and the role of artificial intelligence. This report is critical as Microsoft has a tremendous global vantage point that allows others to gain visibility into the attack activity it sees. For example, the report provides that Microsoft processes more than 78 trillion security signals per day, from billions of Windows endpoints, the cloud, and a broad spectrum of products and services.
Standout Topics
After reviewing 114 pages of critical and informed analysis, the following topics below stand out:
1. Evolving Cyber Threats
The report outlines significant changes in cyber threats, emphasizing how both state-sponsored actors and cybercriminals are increasingly sophisticated and intertwined in their methods. Some key trends include:
- Ransomware: A 2.75x increase in human-operated ransomware incidents, with attackers commonly exploiting unmanaged devices to infiltrate networks. Common methods include phishing via email, SMS, or voice, underscoring the need for secure device management and vigilance.
- Phishing and QR Code Scams: Phishing scams are increasingly sophisticated, with a notable rise in QR code-based phishing. This method lures users into scanning codes that direct them to malicious websites aimed at stealing credentials.
- Business email compromise (BEC) attacks remain a prevalent threat, with inbox rule manipulation the favored method. The report delved into inbox rule manipulation describing a new variation that has emerged involving manipulation through API/App usage. Instead of using the usual “New-InboxRule” or “Set-InboxRule” commands, the attackers now use “UpdateInboxRules”. This allows them to redirect emails with keywords related to credentials or financial matters to less monitored folders like Spam, Conversation History, or Deleted Items, hiding their fraudulent activity from the user’s immediate view.
- Identity Attacks and Social Engineering: Identity-based attacks are prevalent, especially through password attacks, with over 600 million daily attempts observed by Microsoft. The report highlights adversary-in-the-middle (AiTM) phishing, a tactic used to bypass multifactor authentication (MFA) for unauthorized account access. The report highlights tactics such as (1) using extensive social engineering techniques, including researching an organization to identify targets and then impersonating employees or members on phone calls to trick technical administrators into performing password resets or resetting multifactor authentication (MFA) methods and (2) using device management technologies to push additional malicious tooling, disable/evade security products, or creating new virtual machines inside the organization’s cloud. In addition to asset encryption, the malicious actors target data exfiltration using Azure Data Factory and automated pipelines to extract data to its Secure File Transfer Protocol (SFTP) servers.
2. AI’s Role in Cybersecurity
As AI technologies advance, they are shaping both defense and threat landscapes:
- Defensive Capabilities: AI-driven tools are enabling faster threat detection and response, reducing response times for potential breaches that, without AI, could take an average of 277 days.
- Efficiency Gains: AI is being utilized in sorting support requests, enhancing risk assessment by leveraging organizational knowledge, and learning from past incidents for proactive defenses.
- Enhanced Targeting by Adversaries: Threat actors are also beginning to leverage AI, potentially enhancing the precision and scope of social engineering and identity-based attacks.
- Deepfakes: AI-generated synthetic media aka “deepfakes” have become an issue. The report provides that by 2026, 30% of enterprises expect to no longer consider facial biometric identity verification and authentication solutions to be reliable in isolation because as deepfakes become more common in the business environment, organizations will have to implement countermeasures, such as requiring additional verification for transactions.
3. Key Cybersecurity Recommendations
To combat these evolving threats, the report provides several actionable recommendations:
- Zero Trust Framework: Adopting Zero Trust principles, such as verifying access continuously, limiting permissions, and assuming breach potential, are essential steps for bolstering defenses.

- Passwordless Authentication: Replacing traditional passwords with passkeys or biometric authentication helps reduce vulnerabilities, as password attacks remain a common tactic for attackers.

- Security By Design and Default: Microsoft’s Secure Future Initiative emphasizes the need to embed security in all products from inception and enable security features by default, creating a more resilient digital environment.
Actionable Insights
-
- Enable MFA in all your tenants
- Enable phishing-resistant MFA for your admins
- For all new tenants, start with the strongest security settings possible.
- Test pre-configured security settings, such as security defaults or managed Conditional Access policies, in report-only mode to understand their potential impact before going live.
4. Secure Future Initiative (SFI)
Microsoft launched SFI to reinforce cybersecurity across its operations and ecosystem. Key initiatives include:
- Expansion of Security Teams: The company now dedicates 34,000 engineers to security efforts, the largest cybersecurity project to date.
- Security Skilling Academy: A new academy focuses on educating employees on best practices to maintain robust security at all levels of the organization.
- Principles of SFI:
- Security by Design: Integrate security into the product development process from the outset.
- Secure by Default: Automatically enable core security features, reducing user risk.
- Continuous Security Operations: Maintain ongoing threat monitoring and response.
Conclusion
The report provides essential insights for businesses to strengthen their cybersecurity practices and adapt to the rapidly evolving digital threat landscape. As cyber threats grow increasingly complex, staying proactive and embedding security throughout all digital processes remains critical.
HBS’ Chief Recommendations
- Limit Unmanaged Devices: Restrict access to the corporate network through unmanaged devices to prevent unauthorized access points.
- Enhanced Phishing Awareness: Train employees to recognize sophisticated phishing methods, including QR code-based phishing, and use security tools to monitor for suspicious activity.
- Adopt Passkeys and MFA: Implementing passwordless authentication, particularly passkeys protected by biometric verification, is recommended to counter identity-based threats.
(Image Credit: Microsoft)
Disclaimer
This material is provided for informational purposes only. It is not intended to constitute legal advice nor does it create a client-lawyer relationship between Hall Booth Smith, P.C. and any recipient. Recipients should consult with counsel before taking any actions based on the information contained within this material. This material may be considered attorney advertising in some jurisdictions. Prior results do not guarantee a similar outcome.
Blog Overview
About the Author
Jade Davis
Partner | Tampa Office
T: 813.329.3890
E: jdavis@hallboothsmith.com
Jade Davis focuses her practice on data privacy, cyber security, and construction matters. Jade provides strategic privacy and cyber-preparedness compliance advice and defends, counsels, and represents companies on privacy, global data security compliance, data breaches, and investigations.




Leave a comment
You must be logged in to post a comment.